We released smbexec version 2.0 a few days ago and it comes with some rather large differences from previous versions. For one thing it was completely rewritten in Ruby, for another it now supports multi-threading. While it still maintains all of the functionality of previous versions (remotely dumping hashes from systems or domain controllers, identifying where domain administrators credentials are in use, throwing around obfuscated meterpreters, etc) , I wanted to highlight some of the larger changes and new features in this release.
For those that don’t know what smbexec is or haven’t used it before there was a great derbycon presentation at the 2013 conference found here by Martin Bos (purehate) and Eric Milam (brav0hax). The quick description is that smbexec is a tool that focuses on using native windows functions/features for post exploitation and expanding access on a network after you gain some credentials, whether that be a hash or password for a local or domain account. It allows a pentester to quickly identify targets of interest and gain access to them across large networks without much need to worry about AV and UAC. You can grab the code at the pentestgeek github repo.
Ruby and Multi-threading
With the switch to Ruby from shell there are a bunch of added benefits. The biggest one is multi-threading, which makes a significant difference when pen testing a larger network. Last engagement a few of us were at we were running smbexec with 30 threads and dumped the local SAM, cached, and in memory credentials from about 750 servers in a matter of minutes. In addition to the speed gains there is also a significant increase in logging, when any module runs a debug file is created containing information about the module as well as showing a time stamped line with command issued along with the result. We were also able to remove some of the dependencies previous versions required, added more robust error handling, and designed it in a way that makes adding additional modules/features in the future much much easier.
Here is an example of what version 2.0 looks like using the hashdump module:
Finding Juicy Files and Running Arbitrary Powershell
And with the other changes we also have added two more modules. The first, a module used for finding files, has been extremely useful to me so far on penetration tests. By default it looks for unattend files which, if present, usually have privileged credentials contained within but you can look for anything you want. In addition for looking for other things like passwords.xls (Which I have seen way too many times) I personally look for something like *financ*.xls* to look for data that would be considered critical to the business. It can make showing the impact of a vulnerability a lot easier if you have access to nothing but a bunch of workstations for instance. The results of this module can get VERY large, in the thousands per machine even, if you decide to look for something vague like *.xls or *.doc so the results are saved into text files within the log directory so you can use some command line fu to parse the data to look for what you want.
File Finder Module:
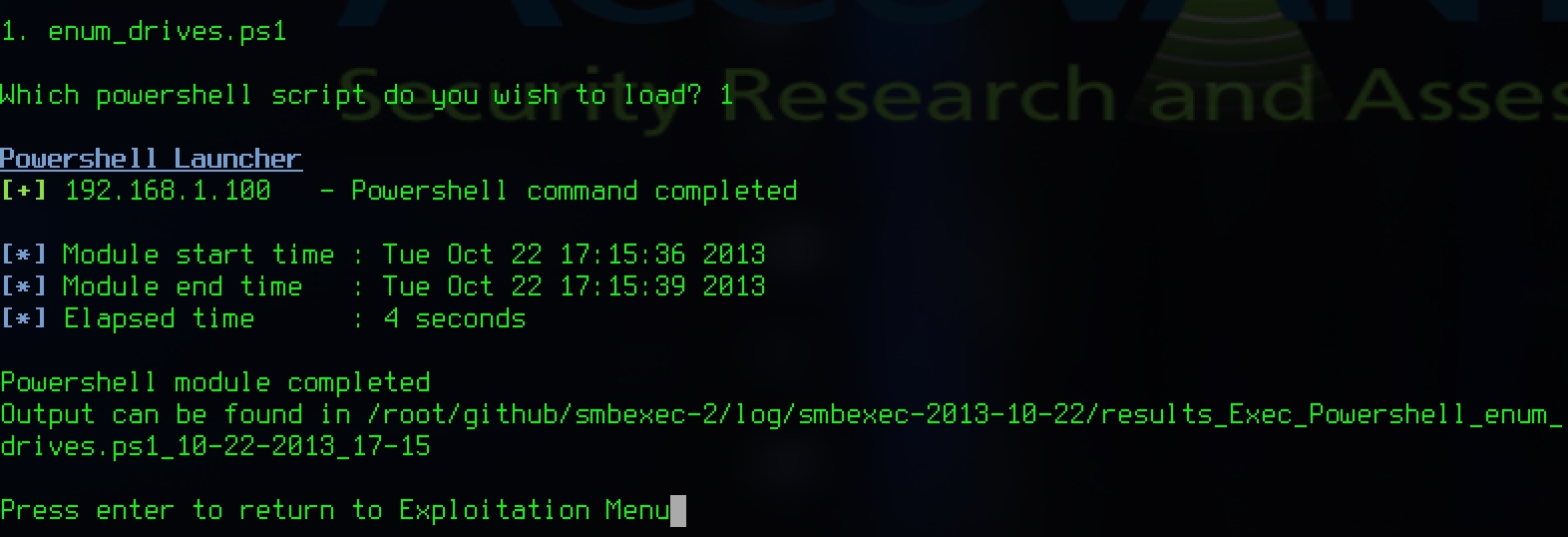
The other module can deliver and run arbitrary powershell against the targets. To do this you only need to drop whatever is your favorite non-interactive powershell script into the powershell folder and it will be available for use. Currently there is only one very simple powershell script but we plan on expanding on this in the future. The results of the powershell script will be saved into text files within the log directory as well.
Powershell Module:
Config and option parser
To make things easier on the user we implemented both a configuration file (smbexec.yml) as well as command line options that should cover most use cases for smbexec. You can give it credentials, an ip range (nmap style supported, or nmap xml file itself), or the number of threads you want to use before starting smbexec and it will remember them for all modules.
These are the command line options:
The configuration file has more granular control over how the tool works, for instance you can set it to use screen sessions over xterm windows or to not use nmap and use a simple TCP full connect port scanner. You also can change the paths to dependencies, by default the configuration file is for a Kali image.
And here is what the smbexec.yml configuration file looks like:
Installation
1) git clone https://github.com/pentestgeek/smbexec.git
2) Run the install.sh script, select your operating system, and supply any required information
3) Run the install.sh script and compile the binaries
4) Type smbexec and cause mass havoc
Wrap up
Now that we have built the framework out in Ruby we should have more updates/features coming up faster and we are already scoping out what we want to do for version 2.1. If you have any issues or feature requests please toss them onto the github page.
The post Smbexec 2.0 released appeared first on Pentest Geek - Penetration Testing - Infosec Professionals.